- Solutions
- Products
- StealthAUDITReporting & Governance
- ---
- Stealthbits App Catalog Browse our catalog of no-charge resource connectors, report packs, and more.
- ---
- StealthDEFENDThreat Detection & Response
- ---
- SbPAMPrivileged Access Management
- ---
- StealthINTERCEPTPolicy Enforcement
- ---
- StealthRECOVERRoll Back & Recovery
- StealthAUDIT
- Support
- Partners
- Company
- Resources
- Login
- Free Trial
Stealthbits
Posts by Jeff Hill

Open Access (Part 2): Shutting It Down
Last week, we talked about the headache-inducing security fault known as Open Access. Now, let us be your Advil. For the past decade, STEALTHbits has been working with many of the largest, most complex organizations in the world to perform content collection and analysis across their technology infrastructure. Through these operations, we have developed an […]

Open Access (Part 1): An Open Bar
There’s a reason Mom and Dad put the liquor in a locked cabinet when my sister and I entered our teenage years. They could make rules, policies, and even threaten discipline, but nothing beats a physical obstacle to enhance security. With some effort and increased risk, we could break into the cabinet, but it made […]

The Wrong Tool for the Job (Rapidly Evolving Data Breach Law – Part 2 of 2…maybe 3)
Two years ago, I met a relative of a friend at a Thanksgiving dinner party. He was a prominent plaintiff’s attorney at a NJ law firm one might recognize from their personal injury commercials; my friend told me previously that he’d done quite well for himself over the years. At my urging – I get […]

Rapidly Evolving Data Breach Law – Part 1 of 2
The raft of enterprise data breaches over the past few years has prompted rapid evolution in Infosec technology, enterprise security philosophy, and has amplified the strategic importance of cybersecurity among corporate leadership. All good stuff. But, as every silver lining has a cloud, and, since we live in the most litigious nation on the planet, […]

Hacking Class is Now in Session
Whoever said crime doesn’t pay wasn’t thinking out-of-the-box, or hasn’t met Ivan Turchynov, the purported leader of a Ukrainian hacking ring recently cracked by US Federal investigators and reported in the Washington Post on August 11th. Apparently, the hackers worked with equity traders to generate upwards of $100MM in profits since 2010 by trading on stolen […]
Location, Location, Location
User behavior analytics (UBA). If it’s not the hottest buzz word in the InfoSec world today, it’s definitely challenging for the top spot. Identifying a security threat, either external or internal, based on activities that vary from a normal pattern is all the rage, and without question, can be a valuable tool in the battle […]

The Icing on the Cake
I was thinking over the weekend about last week’s breach of the UCLA Health System and subsequent theft of 4.5 million medical records. Hackers know that medical records can fetch 10 times the dollars that a stolen credit card can, and that makes sense when you think about it. Cancelling or changing your credit card […]

The IRS Gets Something Worse than an Audit for Using Knowledge Based Authentication
The IRS Get Transcript data leak is evidence of just how complex security at large scales can be. By now I’m sure you’ve heard that at least 100,000 US tax payer’s IRS transcript data has been stolen, and up to 200,000 (possibly many more) were attempted to be stolen. With all the breaches in the […]

Are Security Pros Getting Serious About Security?
I feel better when I exercise. I’d probably do it even if it weren’t really good for my health. Really. But, a nice by-product of my “indulging” in a good Stairmaster workout is improved health. My desire to feel better drives me to exercise, not because I know it’s good for me. Conversely, I know […]
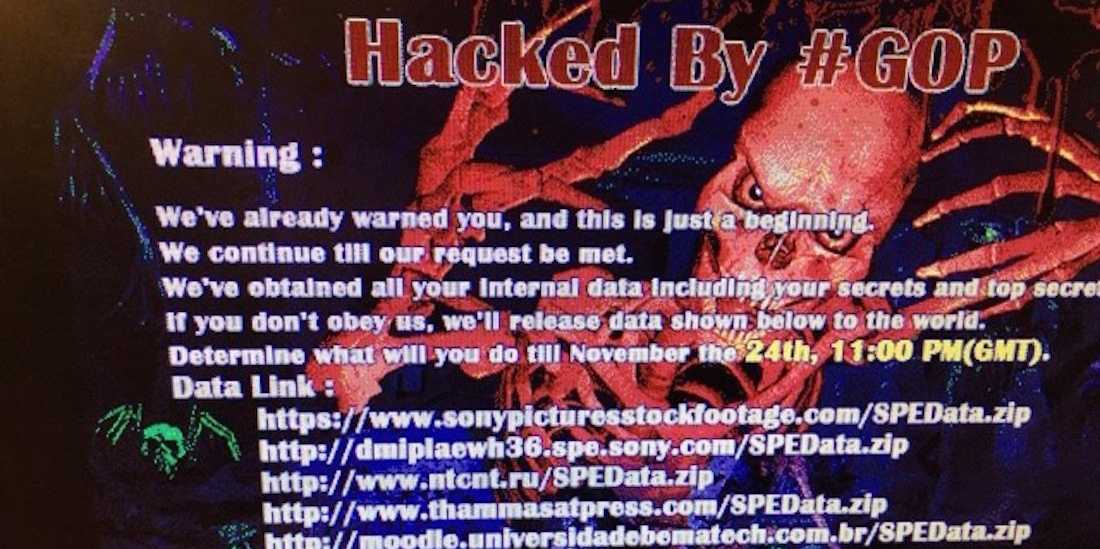
Sony Hack, Unstructured Data, and Privileged Accounts
There are lots of rumors about the Sony Pictures GOP hack right now, but only two things we can say for sure: there was a ton of badly protected unstructured data taken and they used privileged accounts to pull it off. There were documents emerging from as far back as 2000. What were these documents […]
- 1
- 2
Subscribe
DON'T MISS A POST. SUBSCRIBE TO THE BLOG!
© 2022 Stealthbits Technologies, Inc.
