- Solutions
- Products
- StealthAUDITReporting & Governance
- ---
- Stealthbits App Catalog Browse our catalog of no-charge resource connectors, report packs, and more.
- ---
- StealthDEFENDThreat Detection & Response
- ---
- SbPAMPrivileged Access Management
- ---
- StealthINTERCEPTPolicy Enforcement
- ---
- StealthRECOVERRoll Back & Recovery
- StealthAUDIT
- Support
- Partners
- Company
- Resources
- Login
- Free Trial
Advanced Data Security Features for Azure SQL- Part 3: Advanced Threat Protection

In my last blog post, we took a look at the Vulnerability Assessment within the Advanced Data Security (ADS) offering for Azure SQL. In my final blog post of the series, we will take a deep dive into the Advanced Threat Protection features.
Advanced Threat Protection for Azure SQL Databases provides administrators with immediate visibility into potential threats such as suspicious database activities, potential vulnerabilities, SQL injection attacks, as well as anomalous database access and query patterns. Administrators will receive an alert within the Azure Security Center upon the detection of such activities which will include details on the activity and recommended actions on how to investigate and remediate the threat. This feature is available in all Azure SQL Database deployment options, including Managed Instance, Single, and Elastic Pool.
Possible Alerts
The following alerts can be triggered through the use of this feature
- SQL Injection Notifications – Two separate alerts can be triggered related to SQL
Injection
- Vulnerability to SQL Injection – This alert indicates a possible vulnerability to a SQL injection attack, either through a defect in application code that constructs a faulty SQL statement, or when application code or stored procedures don’t sanitize user input when constructing the faulty SQL statement.
- Potential SQL Injection – This alert is triggered when an attacker is trying to inject malicious SQL statements using the vulnerable application code or stored procedure.
- Anomalous Database Access Notifications – Several different alerts fall under this category
including the following
- Access from Unusual Location – This alert is triggered when someone logs on to the SQL server from an unusual geographical location.
- Access from Unusual Azure Data Center – This alert occurs when someone logs onto the SQL server from an unusual Azure data center.
- Access from Unfamiliar Principal – This alert is triggered when someone logs on to the SQL server using an unusual SQL user.
- Access from a Potentially Harmful Application – This alert occurs when a potentially harmful application, such as common attack tools, is used to access the database.
- Brute Force SQL Credentials – This alert occurs when there is an abnormally high number of failed logins with different credentials
In general, these alerts can be triggered by legitimate activities such as new employees or applications, or even penetration testing. However, they can also detect potential threats that are occurring within the Azure SQL environment.
When an alert is triggered, an email notification is sent which provides information on the specific event that took place. This includes the nature of the event, the database name, server name, application name, the event time, as well as investigation and remediation steps.
While remediation steps are provided, these are not automated such as with real-time blocking and may require administrators to take some manual steps.
Enable Advanced Threat Protection
In order to enable Advanced Threat Protection, ADS must be enabled. Refer to my initial blog post in the series for detailed instructions on enabling ADS for your Azure SQL Database. Once enabled, you will have to provide additional information to configure the specific Advanced Threat Protection Settings.
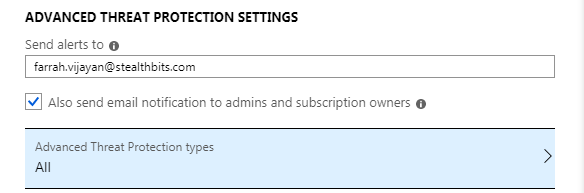
This includes
- The list of email addresses to send alerts to, including the ability to send email notifications to admins and subscription owners
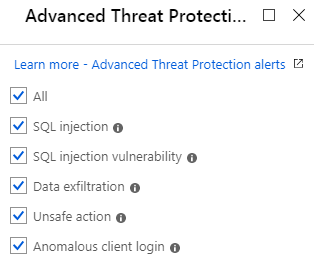
- The Advanced Threat Protection types which includes the ability to choose
- All
- SQL Injection
- SQL Injection Vulnerability
- Data exfiltration
- Unsafe Action
- Anomalous Client Login
While SQL Server and Database Auditing are not required, it is recommended in order to provide a full investigation experience.
You can also configure Advanced Threat Protection by leveraging Azure PowerShell cmdlets. Refer to Microsoft documentation for cmdlets and sample scripts.
Active Alerting
An email will be sent upon occurrence of suspicious activity:
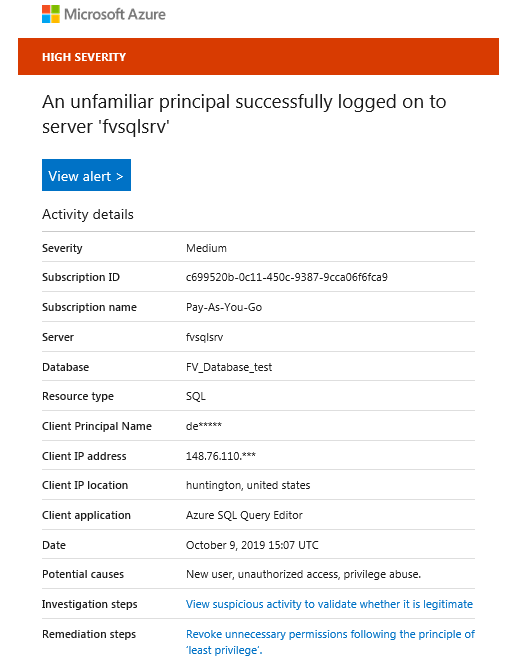
Click the “View alert” button which will bring you to the Azure portal and provide the full alert details.
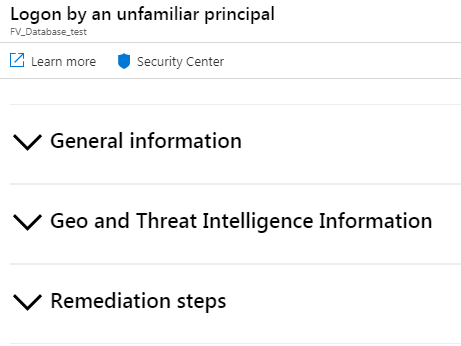
The “General Information” section shows similar details to what is included in the email, along with some additional details.
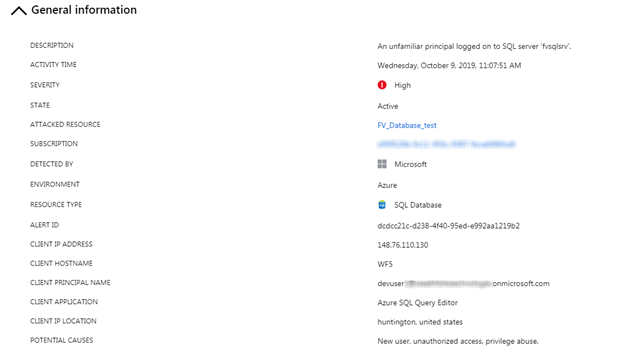
This includes a high-level description of the event, the event time, severity, and other relevant details related to the attacked resource and the suspected attacker, such as the login name and client in the case of an alert related to an unknown login.
The “Geo and Threat Intelligence Information” section provides details on the source location of the attack.

The “Remediation Steps” section provides steps to investigate, recommendations, and steps to remediate.
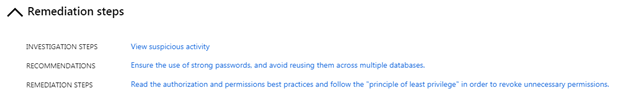
This is where having the server and database auditing feature enabled comes in handy. An admin can choose to “View suspicious activity” which will bring them to the relevant audit records.
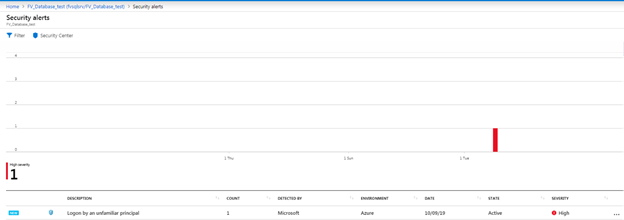
These alerts are also visible through the Azure portal as a notification in the overview section of your database, as well as at the Advanced Data Security section.
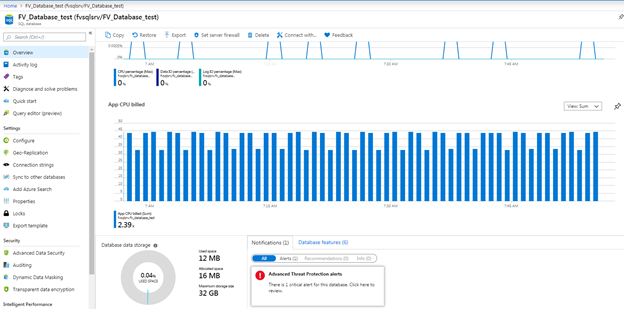
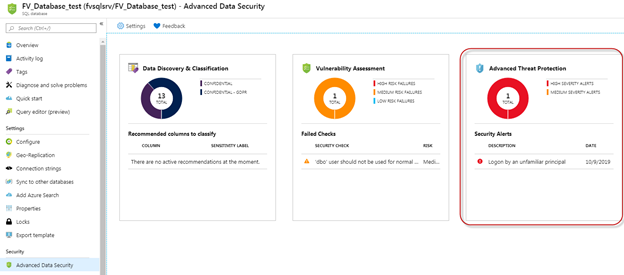
When accessing the alerts through either of these pages, you will be brought to a summary of alerts over the last week, with the ability to drill into specific alerts.
Final Thoughts
The Advanced Data Security offering for Azure SQL provides administrators with a full suite of security functionality to help protect their databases with a single pane of glass view through the Azure Portal.
This blog series highlighted each of the three key features
- Data Discovery & Classification – Discover, classify, label, and protect the data within your Azure SQL databases.
- Vulnerability Assessment – Discover and track potential vulnerabilities and security misconfigurations, with actionable steps that can be taken to fortify your database security posture. The assessment leverages previously applied classifications to offer additional insight into identified vulnerabilities.
- Advanced Threat Protection – Continuously monitor your database for suspicious activity, with real-time alerts on potential vulnerabilities.
To learn about how Stealthbits can help with protecting your SQL databases, visit our website: https://www.stealthbits.com/stealthaudit-for-sql-product

Farrah Gamboa is a Director of Technical Product Management at Stealthbits – now part of Netwrix. She is responsible for building and delivering on the roadmap of Stealthbits products and solutions.
Since joining Stealthbits in 2012, Farrah has held multiple technical roles, including Scrum Master and Quality Assurance Manager. Farrah holds a Bachelor of Science degree in Industrial Engineering from Rutgers University
Related Posts
- What Comes After the FireEye Attack
- Giving Back while Safeguarding Schools in the Age of COVID-19
- Malware’s Growth During the COVID-19 Pandemic
- PostgreSQL Server Security Primer
- Top Data Breaches of 2020
- What is Privacy by Design?
- Data Privacy Essentials: #1 – Don’t Put Your Data at Risk. #2 – Don’t Forget #1
- Data Privacy and Security are Two Sides of the Same Coin
- Easily Prevent More Breaches by Simply Preventing Bad Passwords
- Back to “The Basics” Blog Series
Featured Asset
Stealthbits Credential and Data Security Assessment
Proper data security begins with a strong foundation. Find out what you're standing on with a free deep-dive into the security of your Structured and Unstructured Data, Active Directory, and Windows infrastructure.
Read moreComment
Leave a Reply Cancel reply
Subscribe
DON’T MISS A POST. SUBSCRIBE TO THE BLOG!
© 2022 Stealthbits Technologies, Inc.

This is excellent and easy to understand info and with Screenshot!
Thanks alot!