- Solutions
- Products
- StealthAUDITReporting & Governance
- ---
- Stealthbits App Catalog Browse our catalog of no-charge resource connectors, report packs, and more.
- ---
- StealthDEFENDThreat Detection & Response
- ---
- SbPAMPrivileged Access Management
- ---
- StealthINTERCEPTPolicy Enforcement
- ---
- StealthRECOVERRoll Back & Recovery
- StealthAUDIT
- Support
- Partners
- Company
- Resources
- Login
- Free Trial
Announcing Stealthbits Activity Monitor 3.0 & StealthINTERCEPT 5.1

The Stealthbits team remains keenly focused on delivering world-class activity monitoring and threat analytics solutions to our customers, which is why we are proud to announce the release of Stealthbits Activity Monitor 3.0 and StealthINTERCEPT 5.1. Both of these releases come with several key updates and expanded platform support.
Stealthbits Activity Monitor 3.0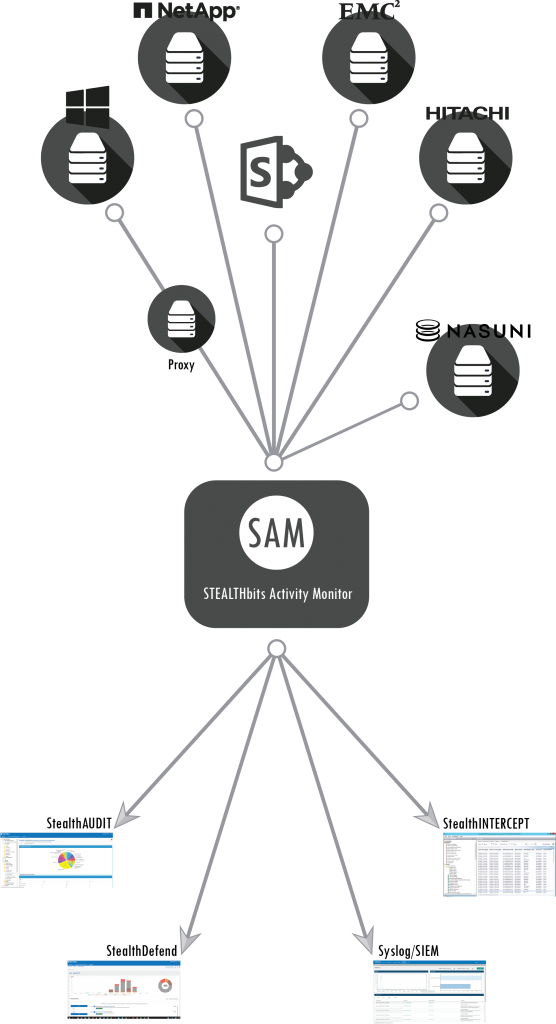
The Stealthbits Activity Monitor provides operational efficiencies and visibility into a wide spectrum of human and machine data interactions with a standardized format.
With the introduction of SharePoint in the Stealthbits Activity Monitor 3.0 release, customers are able to meet a new level of operational and security intelligence that is not available natively within SharePoint.
SharePoint’s monolithic nature allows it to be everything to everyone – it is a Web application, but you can also think of it as a collaboration tool, a document server or even a development framework. The abstract and highly customizable nature of SharePoint is what makes it tough to secure. The ability to monitor SharePoint activity provides a level of operational and security intelligence that is not available natively, including the ability to identify when:
- A document was checked out.
- A document was checked in.
- An object was deleted.
- An object was updated.
- A child object was deleted.
- An object was undeleted.
- A search operation was performed.
- A child object was moved.
- A security group was created.
- A security group was deleted.
- A security principal was added to a security group.
- A security principal was removed from a security group.
Learn more
This is just a highlight of Stealthbits Activity Monitor 3.0, we have added more great features to this release. If you would like to learn more or download a free trial please sign up for our upcoming webinar and visit our product page.
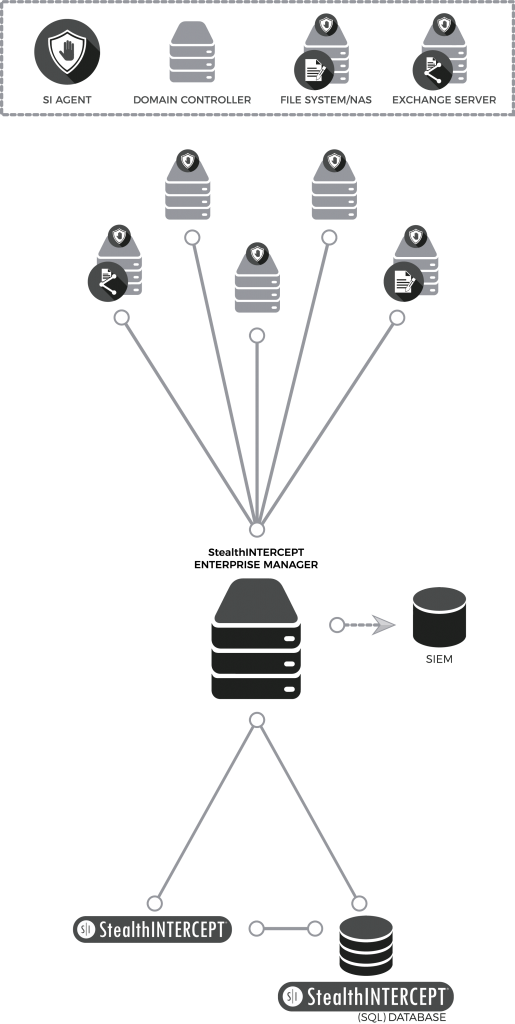 StealthINTERCEPT 5.1
StealthINTERCEPT 5.1
In addition to Stealthbits Activity Monitor 3.0, Stealthbits is also excited to announce the release of StealthINTERCEPT 5.1, providing superior Active Directory protection from modern attacks such as DC SYNC and Forged Privileged Account Certificates (PACs), while also providing operational control of Active Directory.
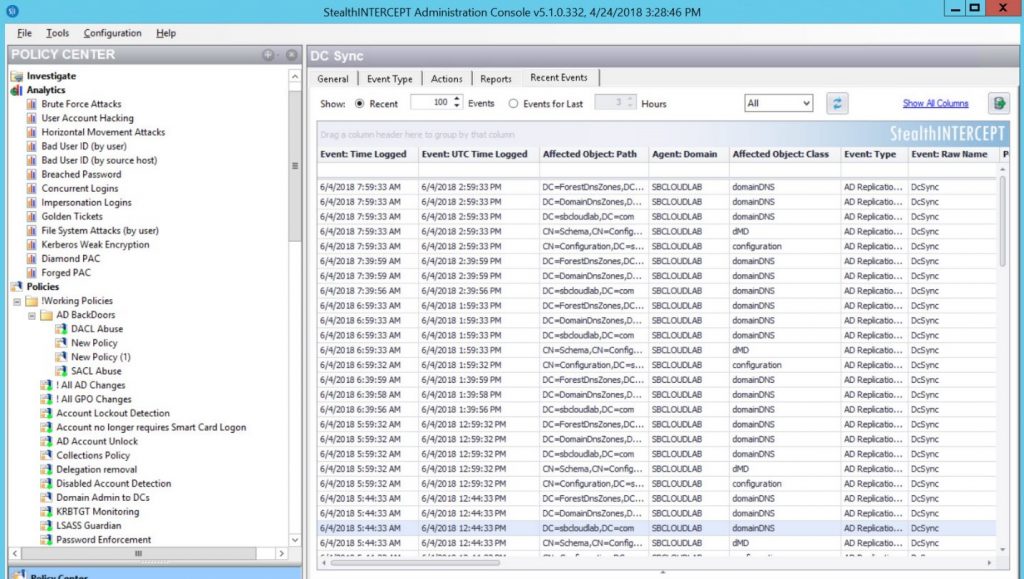
Kerberos-based attacks pose a serious threat to privileged accounts and downgraded encryption methods are a common credential-stealing technique that is used to impersonate users. This new StealthINTERCEPT analytic investigates the Kerberos encryption types used by computers and users and alerts you when a weaker cypher is used, thus providing early detection of a critical insider threat.
Building on our transformation of Active Directory security protection, we studied tools such as the Python Kerberos Exploitation Kit (PyKEK) which are readily available and commonly used by attackers to elevate their privileges within Active Directory. Several of these attacks leverage forged PACs which can be executed without an admin account and can also be performed on any computer on the network (including computers not domain-joined) which poses a serious threat to the entire security of an Active Directory environment. This new StealthINTERCEPT analytic will detect the presence of a manipulated Privileged Attribute Certificate (PAC).
To streamline the protection process, several new preconfigured, out-of-the-box policies have been added to StealthINTERCEPT 5.1 to detect Active Directory Domain Persistence, Privilege Escalation, and Reconnaissance activities. These out-of-the-box policies can be rapidly deployed, customized, configured to block, and forwarded to SIEMs, enhancing an organization’s detection and response capacities.
Learn more
These are just some of the highlights of StealthINTERCEPT 5.1, we have packed a lot more exciting features into this release. If you would like to learn more or download a free trial please sign up for our upcoming webinar and visit our product page.
Don’t miss a post! Subscribe to The Insider Threat Security Blog here:

Gabriel Gumbs is the VP of Product Strategy at STEALTHbits Technologies responsible for end-to-end product vision and innovation. With a 16 year tenure in CyberSecurity, he has spent most of that time as a security practitioner, aligning security innovations with business objectives for Fortune 100 organizations. Gabriel is an information security thought leader, privacy advocate and public speaker.
Related Posts
- Sensitive Data Discovery for Compliance
- Using The Azure Information Protection (AIP) Scanner to Discover Sensitive Data
- Advanced Data Security Features for Azure SQL- Part 1: Data Discovery & Classification
- How to Protect Office 365 by Classifying Your Data with Microsoft’s AIP Labels
- 2019 Verizon DBIR Key Findings
- 5 Cybersecurity Trends for 2019
- EU GDPR: Paving the Way for New Privacy Laws?
- Key Take Aways from the Ponemon 2018 Cost of Insider Threats Report
- Where Real Organizations Are with EU GDPR 10 Days from Launch
- Stealthbits Cyber Kill Chain Attack Catalog: Active Directory Attacks and More
Featured Asset
Stealthbits Credential and Data Security Assessment
Proper data security begins with a strong foundation. Find out what you're standing on with a free deep-dive into the security of your Structured and Unstructured Data, Active Directory, and Windows infrastructure.
Read moreSubscribe
DON’T MISS A POST. SUBSCRIBE TO THE BLOG!
© 2022 Stealthbits Technologies, Inc.

Leave a Reply