- Solutions
- Products
- StealthAUDITReporting & Governance
- ---
- Stealthbits App Catalog Browse our catalog of no-charge resource connectors, report packs, and more.
- ---
- StealthDEFENDThreat Detection & Response
- ---
- SbPAMPrivileged Access Management
- ---
- StealthINTERCEPTPolicy Enforcement
- ---
- StealthRECOVERRoll Back & Recovery
- StealthAUDIT
- Support
- Partners
- Company
- Resources
- Login
- Free Trial
Stealthbits
Posts by Bert Scalzo

Database Security Best Practices – Simple & Worthwhile Concepts – Part IV
Database security is a hot topic these days, especially with all the new and seemingly never-ending security compliance requirements being imposed such as GDPR. This means that organizations and their DBAs must step up their game when it comes to database security. Some DBAs may think these new requirements apply only to production but depending […]

Database Security Best Practices – Simple & Worthwhile Concepts – Part III
Database security is a hot topic these days, especially with all the new and seemingly never-ending security compliance requirements being imposed such as GDPR. This means that organizations and their DBAs must step up their game when it comes to database security. Some DBAs may think these new requirements apply only to production but depending […]

Database Security Best Practices – Simple & Worthwhile Concepts – Part II
Database security is a hot topic these days, especially with all the new and seemingly never-ending security compliance requirements being imposed such as GDPR. This means that organizations and their DBAs must step up their game when it comes to database security. Some DBAs may think these new requirements apply only to production but depending […]

Database Security Best Practices – Simple & Worthwhile Concepts – Part I
Database security is a hot topic these days, especially with all the new and seemingly never-ending security compliance requirements being imposed such as GDPR. This means that organizations and their DBAs must step up their game when it comes to database security. Some DBAs may think these new requirements apply only to production but depending […]
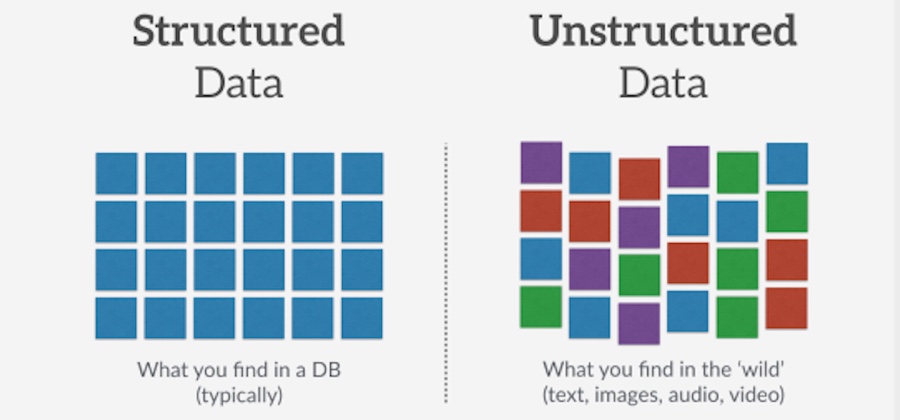
Securing Structured Data
Editor’s Note: Read this related blog:“The Structured Future of Data Access Governance“. There are generally two kinds of data: structured and unstructured. An oversimplification shown in Figure 1 below is essentially correct. When we say, “structured data”, we usually mean traditional data that possess organized layouts with somewhat predictable growth characteristics. In fact, for relational […]
The Structured Future of Data Access Governance
When Data Access Governance (DAG) was first conceived, the logical place to implement such access control was on unstructured data such as shared file systems, collaborative platforms (e.g. SharePoint), and email systems. These massive unstructured data repositories seemingly contained the bulk of the corporate data, often quoted as representing well over 80% of all corporate […]
Subscribe
DON'T MISS A POST. SUBSCRIBE TO THE BLOG!
© 2022 Stealthbits Technologies, Inc.
