- Solutions
- Products
- StealthAUDITReporting & Governance
- ---
- Stealthbits App Catalog Browse our catalog of no-charge resource connectors, report packs, and more.
- ---
- StealthDEFENDThreat Detection & Response
- ---
- SbPAMPrivileged Access Management
- ---
- StealthINTERCEPTPolicy Enforcement
- ---
- StealthRECOVERRoll Back & Recovery
- StealthAUDIT
- Support
- Partners
- Company
- Resources
- Login
- Free Trial
Stealthbits
Posts by Gabriel Gumbs

ProTip – Protecting Sensitive Data Step-up Authentication
In prior ProTips we have explored discovering sensitive data throughout the environment, managing access to that data and monitoring it. Today’s ProTip focuses on adding an additional layer of protection that protects sensitive data in the event of a Ransomware outbreak, or compromised credentials being used to steal data. Creating the Investigation First, we create […]
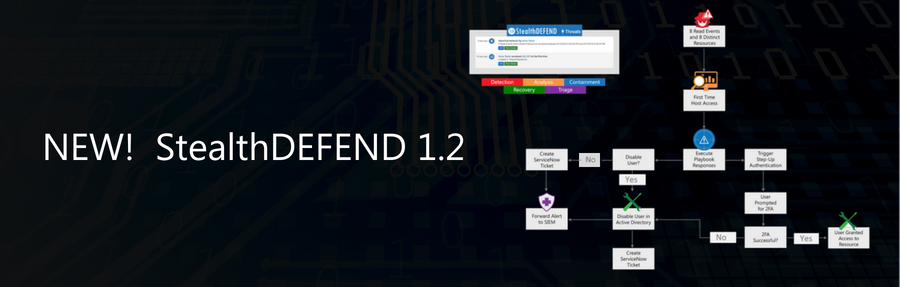
How Threat Analysts have Become Superstitious: Superstition vs. Machine Learning with StealthDEFEND v1.2
The American psychologist B. F. Skinner conducted an experiment to examine how superstitions are formed. Using one of his favorite test subjects, pigeons, he observed that the pigeons associated whatever chance actions they had been performing when they were fed. Some of the birds would turn twice, while others would peck three times and they […]

Authentication Attacks Have You Worried? Me Too… Introducing StealthINTERCEPT 5.2
Those of you that are familiar with STEALTHbits know that protecting credentials is in our DNA – there is no separating credential protection from a sane data protection strategy. The operative word being “sane”. Earlier this year we introduced the first iteration of our Enterprise Password Enforcer, a password policy enforcement tool for Active Directory. […]

Market Trends: Privileged Access and Insider Threats
Halfway through the year, 2018 has seen an increase of insider threats that continue to highlight how privileged access is easily abused for a variety of nefarious activities. Tesla, the electronic car manufacturer, was hit by an insider that used their access to sabotage systems and give away trade secrets. A Punjab National Bank employee […]

Announcing Stealthbits Activity Monitor 3.0 & StealthINTERCEPT 5.1
The Stealthbits team remains keenly focused on delivering world-class activity monitoring and threat analytics solutions to our customers, which is why we are proud to announce the release of Stealthbits Activity Monitor 3.0 and StealthINTERCEPT 5.1. Both of these releases come with several key updates and expanded platform support. Stealthbits Activity Monitor 3.0 The Stealthbits […]

GDPR–A Crash Course
Well Ladies and Gentlemen, GDPR is finally upon us. I say finally because we have collectively been studying, reviewing, preparing and planning for this day for quite some time now. I know that not everyone is ready. And the European Commission equally knows that not everyone is ready. That is not an invitation to flaunt […]
Announcing StealthDEFEND 1.1
Point releases are not usually a big deal. And while we could have quietly released the latest version of our real-time threat analytics and alerting component of the STEALTHbits’ Data Access Governance suite, the team worked hard to incorporate the feedback we received and make significant strides. The cyber security industry skills gap continues to […]

2018 Threat Hunting Report
67% of organizations are not confident in their ability to uncover insider threats? In response to new challenges, threat hunting is a developing security practice that focuses on proactively detecting and isolating advanced threats. Detecting, preventing and mitigating “insider threats” is the most common reason for an organization to have a threat hunting program. However, […]

A Tale of One City – Data Privacy Day
Data Privacy Day is among us, and for that matter so is EU GDPR and NYCRR 500. What do these all have in common? Well, privacy. Privacy by design really should be more than just the mantra of GDPR, it needs to become the mantra of everyone handling any type of customer information. I do […]

Market Trends: Announcing StealthINTERCEPT 5.0 General Availability – With Enterprise Password Enforcer & LSASS Guardian™
Transforming Active Directory Security Five years ago we introduced the StealthINTERCEPT product line, to address the growing requirement for a comprehensive Active Directory change and access monitoring solution. We know that Active Directory is safest when it is clean, properly configured, closely monitored, and tightly controlled – that is exactly what StealthINTERCEPT has been successfully […]
Subscribe
DON'T MISS A POST. SUBSCRIBE TO THE BLOG!
© 2022 Stealthbits Technologies, Inc.
