- Solutions
- Products
- StealthAUDITReporting & Governance
- ---
- Stealthbits App Catalog Browse our catalog of no-charge resource connectors, report packs, and more.
- ---
- StealthDEFENDThreat Detection & Response
- ---
- SbPAMPrivileged Access Management
- ---
- StealthINTERCEPTPolicy Enforcement
- ---
- StealthRECOVERRoll Back & Recovery
- StealthAUDIT
- Support
- Partners
- Company
- Resources
- Login
- Free Trial
Stealthbits
Posts by Jeff Warren
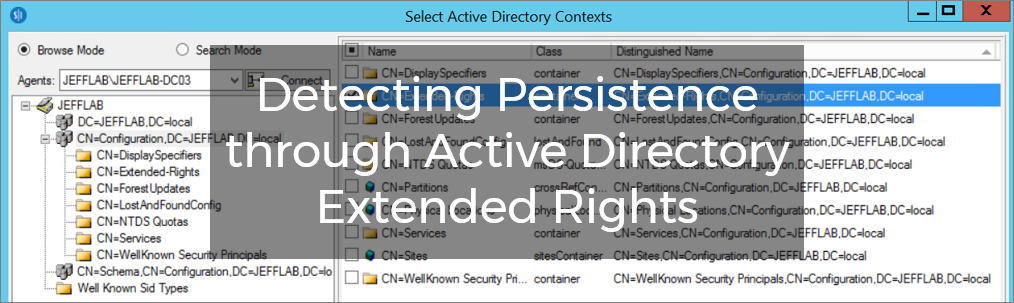
Detecting Persistence through Active Directory Extended Rights
Today, I came across an interesting article (since posting, the original post has been taken offline) where the author described how an attacker could manipulate the permissions on extended attributes to create persistence once they have compromised an Active Directory domain. Read the article for a great breakdown of the attack, but here’s a quick […]
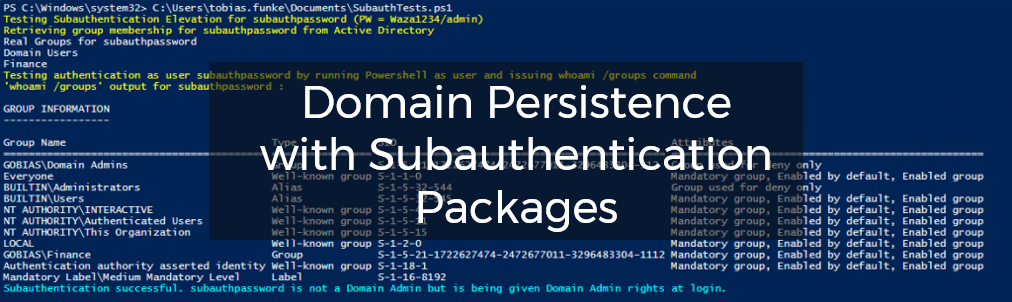
Domain Persistence with Subauthentication Packages
A lot of my posts have covered Mimikatz and how it can be used to explore Active Directory and Windows security to learn how various attacks work. Recently, the author of Mimikatz released a new feature which exposes a new attack surface that could be used to create persistence within AD. This feature uses a […]

How to Detect Pass-the-Hash Attacks
This is the first in a 3-part blog series, that will be followed by a webinar February 28th. Lateral movement techniques are one of the most common approaches attackers can use to infiltrate your network and obtain privileged access to your credentials and data. This has been seen recently with modern ransomware such as SamSam and […]

Creating Persistence with DCShadow
Now that we understand the basics of the DCShadow feature, let’s look at some ways in which attackers can leverage DCShadow in a real world attack scenario. As we learned, DCShadow requires elevated rights such as Domain Admin, so you can assume an attacker leveraging this already has complete control of your environment. So why […]
Attacking Weak Passwords in Active Directory
In our last post, we learned about password spraying and how effective this can be to compromise AD accounts with weak and commonly used passwords. Now let’s take a look at how an attacker could take this approach and put it into practice to compromise your domain. For that, we are going to use BloodHound, […]
Finding Weak Passwords in Active Directory
So far in this series we’ve looked at how plain text passwords can be exposed within Active Directory, which represents a major vulnerability for most AD environments. However, even if you have proper controls to prevent plain text passwords in your network, attackers can still get them pretty efficiently. How do they do this? They […]
4 Active Directory Password Attacks and How to Protect Against Them
Active Directory Password Attacks So far in our travels through Active Directory security, we’ve looked at attacks against permissions, credentials, service accounts, and many of the open-source toolkits available for getting more hands-on exposure to these techniques. Inside each scenario, an attacker is attempting to increase their privileges and compromise sensitive information. Some techniques like […]

How Attackers Are Bypassing PowerShell Protections
Bypassing PowerShell Protections Now that we have explored various protections against malicious PowerShell, let’s look at how to get around every one of these PowerShell protections! Don’t worry, these PowerShell protections are still worth doing, and they will still make things harder on attackers and easier to detect. However, we need to be aware that […]

How Attackers are Stealing Your Credentials with Mimikatz
Stealing Credentials with Mimikatz Mimikatz is an open-source tool built to gather and exploit Windows credentials. Since its introduction in 2011 by author Benjamin Delpy, the attacks that Mimikatz is capable of have continued to grow. Also, the ways in which Mimikatz can be packaged and deployed have become even more creative and difficult to […]

Extracting User Password Data with Mimikatz DCSync
Introduction: Extracting User Password Data with Mimikatz DCSync Mimikatz provides a variety of ways to extract and manipulate credentials, but probably one of the most useful and scary ways is using the DCSync command. This attack simulates the behavior of a domain controller and asks other domain controllers to replicate information using the Directory Replication Service […]
- 1
- 2
Subscribe
DON'T MISS A POST. SUBSCRIBE TO THE BLOG!
© 2022 Stealthbits Technologies, Inc.
