- Solutions
- Products
- StealthAUDITReporting & Governance
- ---
- Stealthbits App Catalog Browse our catalog of no-charge resource connectors, report packs, and more.
- ---
- StealthDEFENDThreat Detection & Response
- ---
- SbPAMPrivileged Access Management
- ---
- StealthINTERCEPTPolicy Enforcement
- ---
- StealthRECOVERRoll Back & Recovery
- StealthAUDIT
- Support
- Partners
- Company
- Resources
- Login
- Free Trial
Stealthbits
Posts by Jonathan Sander

National Cyber Security Awareness Month (NCSAM) – Week 5 – Protecting Critical Infrastructure From Cyber Threats
If you haven’t heard, October was National Cyber Security Awareness Month (NCSAM). NCSAM is sponsored by U.S. Department of Homeland Security and the National Cyber Security Alliance, and each week of the month has a different theme. The STEALTHbits team observed the month with a new blog post on the theme each week. So stay tuned […]

National Cyber Security Awareness Month (NCSAM) – Week 3 – Today’s Predictions for Tomorrows Internet
If you haven’t heard, October is National Cyber Security Awareness Month (NCSAM). NCSAM is sponsored by U.S. Department of Homeland Security and the National Cyber Security Alliance, and each week of the month has a different theme. The STEALTHbits team will be observing the month with a new blog post on the theme each week. […]

National Cyber Security Awareness Month (NCSAM) – Week 2 – Cybersecurity in the Workplace Is Everyone’s Business
If you haven’t heard, October is National Cyber Security Awareness Month (NCSAM). NCSAM is sponsored by U.S. Department of Homeland Security and the National Cyber Security Alliance, and each week of the month has a different theme. The STEALTHbits team will be observing the month with a new blog post on the theme each week. […]
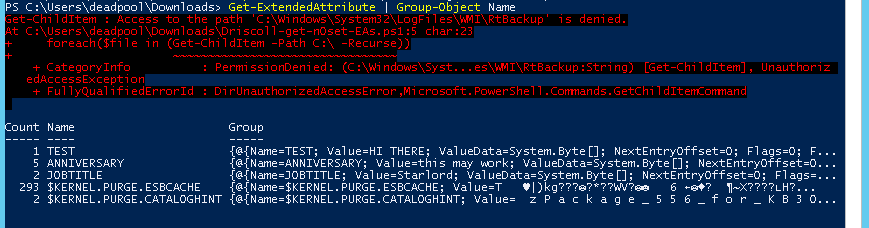
Attack Step 3: Persistence with NTFS Extended Attributes – File System Attacks
What Does Persistence Mean on a File System? In our first file system attack, we found places where we’re likely to get good data with the credentials we’ve been able to steal. Our second attack let us focus in on only the data that is worth the time to steal so we can lessen the […]

National Cyber Security Awareness Month (NCSAM) – Week 1 – Simple Steps to Online Safety
If you haven’t heard, October is National Cyber Security Awareness Month (NCSAM). NCSAM is sponsored by U.S. Department of Homeland Security and the National Cyber Security Alliance, and each week of the month has a different theme. The STEALTHbits team will be observing the month with a new blog post on the theme each week. […]

Attack Step 2: Targeting Interesting Data – File System Attacks
Sifting Through The Sands In the last post, we looked at how to find file shares where data we may want to steal lives. We used both Python-based and PowerShell based approaches to this. Now we’re going to take the next step and find actual files of interest. Even the smallest organization can have many […]

Stealthbits at Microsoft Ignite 2017 – Insider Threat Podcast #8
In our eight edition of the Insider Threat Podcast, we spoke with the most senior member of the Stealthbits team, Adam Laub. Adam had just been to the Microsoft Ignite conference and brought us some insight into what the pulse of the show was. We brought our new focus on Threat Protection to the show […]

Attack Step 1: Finding Where Data Lives – File System Attacks
Finding Where Interesting Information May Live We’re going to make some assumptions at the start of this attack. We will assume we already have full access to any credentials we need. Why? Because we’ve already shown you how you can grab any credential you might need all the way up to the highest level of […]

File System Attacks
Credentials Are the Means to Attack Data If you’ve been reading the attack blog series until now, you’ve seen we have focused on attacks against Active Directory – like attacking core AD infrastructure, leveraging AD service accounts to attack, attacking AD with misconfigured permissions, and our series on Mimikatz attacks. Of course, AD is the […]

Stealing Sensitive Data One User at a Time: The Unlikely Headline
Sensitive Data Attacks vs. Typical Headlines As I write this, you are likely reading something about the Equifax breach. The attention it is getting is well-deserved. So many millions of personal records and sensitive data exposed are always a cause for concern. However, it feeds an unhealthy cycle. Huge breaches happen when attackers break a […]
Subscribe
DON'T MISS A POST. SUBSCRIBE TO THE BLOG!
© 2022 Stealthbits Technologies, Inc.
