- Solutions
- Products
- StealthAUDITReporting & Governance
- ---
- Stealthbits App Catalog Browse our catalog of no-charge resource connectors, report packs, and more.
- ---
- StealthDEFENDThreat Detection & Response
- ---
- SbPAMPrivileged Access Management
- ---
- StealthINTERCEPTPolicy Enforcement
- ---
- StealthRECOVERRoll Back & Recovery
- StealthAUDIT
- Support
- Partners
- Company
- Resources
- Login
- Free Trial
Stealthbits
Posts by Mark Wilson

5 Essential Steps to EU GDPR – Part 5: GDPR The Ticking Time Bomb
At the time of writing this blog, there are 378 days, 8 hours until the GDPR comes into force. That’s 54 weeks or approximately 270 weekdays, not considering public holidays. Surely plenty of time to get everything in place and ensure your business is compliant. Right? Wrong! Let me back this up by putting some context around […]

5 Essential Steps to EU GDPR – Part 4: Stealthbits Technologies, a logical fit for EU GDPR
In part three we discussed how no one person, organization or vendor has ‘the’ silver bullet to GDPR compliance. What you need is an array of tools and people to address the many challenges ahead. Saying that not all technical solutions are equal in their value to a GDPR project. Given GDPR is a Data Governance […]

5 Essential Steps to EU GDPR – Part 3: Engage the Right People
This is arguably the most important element in achieving GDPR compliance. No organisation can do everything independently. Even software vendors must engage with outside agencies on this one. We’re going to discuss ‘the right people’ as two categories; Internal and External. If ever there was an all hands requirement in a project, this is it. […]

5 Essential Steps to EU GDPR – Part 2: GDPR, the Data Access Governance Project
In part one we looked at the questions organisations must address when dealing with DSARs (Data Subject Access Request). Simple questions, but in reality, tricky or virtually impossible to answer depending on the size and complexity of your data infrastructure. That said, they’re actually the core premise of Data and Access Governance. What is Data […]

5 Essential Steps to EU GDPR
Part 1: Understand the Basic Requirements of GDPR Despite the GDPR being marked as a clearer to understand regulation, it’s still a mine field of legal and compliance requirements, interpretations and uncertainty. The purpose of this blog series is to help you understand the fundamental requirements of GDPR by peeling back the layers of legality, […]
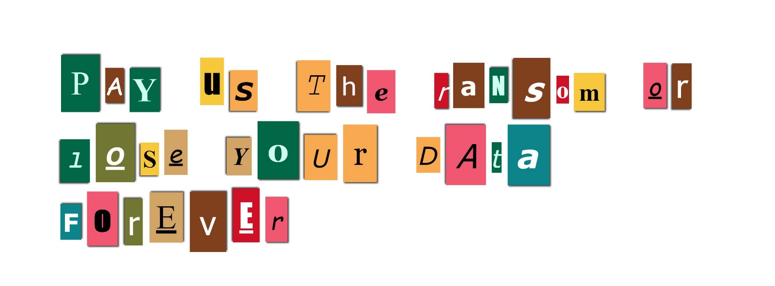
Eliminate the Threat of Ransomware
Knowledge and understanding are everything in the fight against ransomware, so before we go any further, you should check out these two previous STEALTHbits blog posts: Protecting against Ransomware The five most prevalent threats to corporate data Understanding the basics of how ransomware works and the motivations behind it is essential to fight the threat. […]

Ransomware: Get to the Point.
The proliferation of Ransomware continues apace, which is no surprise given the motivation is monetary. Wherever there’s something of value that can be exploited, it will be exploited. Every organization has to take the threat of Ransomware seriously and address the risk head-on. Where do you start? You start with the basics: understanding what’s at risk and […]

Effective Nested Group Membership Changes
Real-Time Auditing of the Classic Insider Threat A Russian Nesting Doll? What a bizarre choice of image to accompany a technology blog, you may think. In the same way that you can’t determine what is contained within a nest of Russian Dolls, without opening them up, Active Directory doesn’t reveal exactly who is a member […]

Microsoft Exchange, Operation-Level Auditing: Auditing the Insider Threat
Do you have sensitive data in your Exchange mailbox? What would happen if your mailbox was accessed with malicious intent? The first step to mitigating your risk is to know if an unauthorized person has accessed your mailbox. You don’t need to know what the burglar is trying to steal to know they’re in your house. The […]

Market Trends: ‘Millions of Email Accounts Compromised…’
‘Millions of Email Accounts Compromised…’ – The Daily Telegraph (UK), May 2016 This was the headline in a UK news outlet discussing a ‘…massive data breach that includes Google and Yahoo’. It’s a catchy headline for sure. However, the line that really caught my attention was from the lead paragraph: ‘More than 270 Million email accounts […]
- 1
- 2
Subscribe
DON'T MISS A POST. SUBSCRIBE TO THE BLOG!
© 2022 Stealthbits Technologies, Inc.
