- Solutions
- Products
- StealthAUDITReporting & Governance
- ---
- Stealthbits App Catalog Browse our catalog of no-charge resource connectors, report packs, and more.
- ---
- StealthDEFENDThreat Detection & Response
- ---
- SbPAMPrivileged Access Management
- ---
- StealthINTERCEPTPolicy Enforcement
- ---
- StealthRECOVERRoll Back & Recovery
- StealthAUDIT
- Support
- Partners
- Company
- Resources
- Login
- Free Trial
File System Auditing

File System Auditing
Adequately and efficiently capturing file system access and change activities can dramatically increase an organization’s ability to detect insider threats, prevent data breaches, and mitigate the damage that can be done by advanced threats like crypto ransomware. Native file system auditing functions within file repositories like Windows file servers and NAS devices like NetApp and Dell/EMC, however, are highly challenging to work with – sometimes impossible – often resulting in a significant blind spot for security practitioners and IT operations personnel.
Top Use Cases for File System Auditing
The importance of capturing file system activity cannot be understated, having far-reaching benefits from Ransomware detection to forensic investigations, all of which lead to greater security and efficiency for an organization.
- File Auditing for Governance – In the context of a properly crafted Data Access Governance program, file activity can tell you just as much about what users don’t need access to, as it does about what they do need access to. Capturing and analyzing file activity over an extended period of time, provides invaluable insight into how users are actually leveraging their access privileges, enabling the proactive removal of unused access rights that overexpose organizations to insider threats, and of course, Ransomware.
- File Auditing for Forensics – Because so many organizations struggle to even turn native file system auditing on (let alone tune it properly), most SIEM deployments are void of file activity information from all the places file activity is occurring. Outside of file system data being involved in a high number of data breaches cases, the lack of file activity data within SIEM means forensic investigations are often foiled by a significant lack of evidence. Adding insult to injury, the data generated out of file system auditing logs is often missing key event attributes, is cluttered with noise events, and in some cases is entirely incomprehensible. Nevertheless, getting file system activity into SIEM is a boon for security and critical to knowing what data was taken, if successfully exfiltrated.
- File Auditing for Storage Operations – Storage Admins have a difficult job. As if ensuring file storage availability isn’t tough enough, storage teams are often bombarded with questions originating from end-users like, “Where’d my file go?” or “I could access this folder yesterday. Why can’t I today?” These seemingly simple questions are hardly simple to answer without file system auditing enabled. However, with a clean audit trail of activity, Storage Admins won’t need to answer these questions anymore because the helpdesk could easily accomplish the task on their behalf.
- File Auditing for Ransomware Detection – Ransomware can present itself and potentially be caught at multiple levels within the attack chain (e.g. Phishing email, AV at the endpoint, etc.), but there’s no more telltale sign of a Ransomware attack underway than observing troves of files encrypted in seconds. Literally every second counts in the midst of a Ransomware assault and monitoring file activity is arguably the most logical type of activity to be monitoring for in a Ransomware context.
Just in these examples alone, there are at least three major beneficiaries of the visibility file system auditing can provide, including Security, Storage Operations, and Governance teams.
Top File System Auditing Challenges
It’s easy to see that auditing file system activity is a worthwhile concept and for multiple reasons; so why doesn’t everyone do it? Here’s what it ultimately boils down to, but I’d highly suggest reading this White Paper called “5 Challenges with Monitoring Windows File Activity” for some specifics:
- Performance – Enabling file system auditing is like turning on a fire hose. The number of events generated through native file system audit log
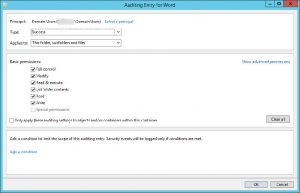 ging is staggering, causing logs to roll and disks to fill up. Just the act of a single user opening, editing, saving, and closing a Word document on a Windows File Share generates 230 events in the event log! Furthermore, there are very limited filtration capabilities, making it impossible to exclude something like a noisy process or individual account from being logged. Essentially, the events pile up, machine performance degrades, people complain, and the opportunity is lost.
ging is staggering, causing logs to roll and disks to fill up. Just the act of a single user opening, editing, saving, and closing a Word document on a Windows File Share generates 230 events in the event log! Furthermore, there are very limited filtration capabilities, making it impossible to exclude something like a noisy process or individual account from being logged. Essentially, the events pile up, machine performance degrades, people complain, and the opportunity is lost. - Data Quality – If enabling file system auditing is like turning on a fire hose, then trying to understand the data it produces is like drinking from one (except more painful). First, it’s important to note that a large portion of the data generated through native file system auditing is garbage. Temporary Files with their fancy tilde’s (~) top the list. Second, the necessity to correlate multiple events to figure out a file moved from one folder to another or translate Security Descriptor Definition Language (SDDL) to decipher the details of a permissions change, is just plain difficult to do.

So, that’s why everyone doesn’t do it. It causes them grief and understanding the output is like another full-time job.
File System Auditing Alternatives
So far, we’ve discussed many of the merits of monitoring file activity on your Windows and NAS devices, as well as some of the hurdles to making it happen.
You can dedicate the time, resources, and money to ensure critical systems have the horsepower they need to churn out the data, stuff it all into SIEM (even the garbage data), brush up on your Event Log knowledge, and write your rules and correlation routines, but that’s a pretty expensive proposition.
Alternatively, you could use a highly tuned, intelligent file system auditing alternative like STEALTHbits File Activity Monitor. It’s lightweight, easy-to-use, scalable, configurable, affordable, and interoperable with your SIEM (check out the IBM QRadar and Splunk apps that come along with it for free).
Learn more about STEALTHbits File Activity Monitor.
Don’t miss a post! Subscribe to The Insider Threat Security Blog here:

As General Manager, Adam is responsible for product lifecycle and market adoption from concept to implementation through to customer success. He is passionate about market strategies, and developing long-term path for success for our customers and partners.
Previously, Adam served as CMO and has held a variety of senior leadership positions at Stealthbits – now part of Netwrix including Sales, Marketing, Product Management, and Operational Management roles where his focus has consistently been setting product strategy, defining roadmap, driving strategic engagements and product evangelism.
Adam holds a Bachelor of Science degree in Business Administration from Susquehanna University, Selinsgrove, PA.
Related Posts
- Sensitive Data Discovery for Compliance
- Using The Azure Information Protection (AIP) Scanner to Discover Sensitive Data
- Advanced Data Security Features for Azure SQL- Part 1: Data Discovery & Classification
- How to Protect Office 365 by Classifying Your Data with Microsoft’s AIP Labels
- 2019 Verizon DBIR Key Findings
- 5 Cybersecurity Trends for 2019
- EU GDPR: Paving the Way for New Privacy Laws?
- Announcing Stealthbits Activity Monitor 3.0 & StealthINTERCEPT 5.1
- Key Take Aways from the Ponemon 2018 Cost of Insider Threats Report
- Where Real Organizations Are with EU GDPR 10 Days from Launch
Featured Asset
Stealthbits Credential and Data Security Assessment
Proper data security begins with a strong foundation. Find out what you're standing on with a free deep-dive into the security of your Structured and Unstructured Data, Active Directory, and Windows infrastructure.
Read moreSubscribe
DON’T MISS A POST. SUBSCRIBE TO THE BLOG!
© 2022 Stealthbits Technologies, Inc.

Leave a Reply