- Remote registry needs to be enabled on the target host

- One of two security parameters need to be set
- The account being leveraged needs to be a member of the Backup Operators group on the target host, or, in the case of a domain controller, the ID would need to be added the builtinbackup operators group for the domain.
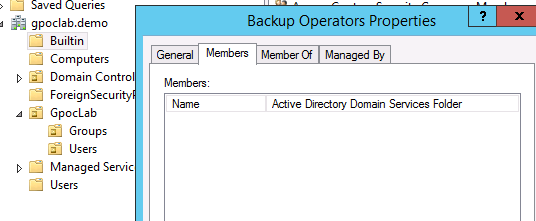
- If the client does not want to elevate the ID to backup operators, the ID would have to be given read access to this target host registry hive location directly: HKLMSYSTEMCurrentControlSetControlSecurePipeServers winreg
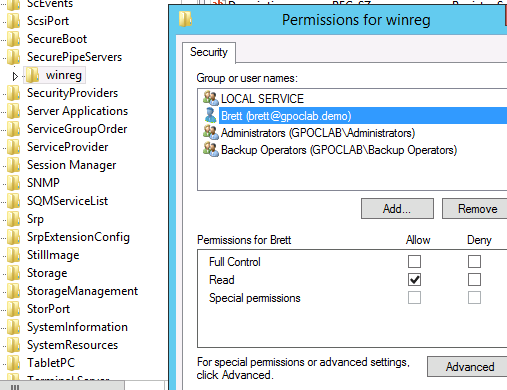
Once these two requirements are met, StealthAUDIT can audit any registry hive that is open to Authenticated Users.


Leave a Reply