Microsoft SharePoint is one of the most popular platforms for collaboration and content sharing within internal teams and even with external users. Therefore, ensuring SharePoint security is vital to helping your company avoid costly data breaches and business disruptions. This article details the key best practices for protecting your SharePoint sites, whether you are using on-prem SharePoint Server or SharePoint Online version.
Use groups to manage user permissions.
The best practice for granting access to any IT resources is for admins not to assign permissions directly to a user, but instead assign permissions to groups and grant each user membership in the appropriate groups. This approach makes provisioning, reprovisioning and deprovisioning simpler and helps ensure that permission levels are in line with the least-privilege principle. In the case of SharePoint, you can assign permissions to either a SharePoint site group or an Active Directory security group.
One group that you should avoid is the infamous “Everyone” group — it includes all current network users, including guests and users from other domains, and its membership cannot be modified.
Depending on which SharePoint platform you are using, there are additional groups that should be avoided because they include a large set of users:
SharePoint Server:
- NT AUTHORITY\Authenticated Users — Includes all AD user accounts from all domains in the forest and therefore cannot be managed at the domain level.
- DOMAIN\Domain Users — Includes all user accounts in the domain.
SharePoint Online:
- Everyone except external users — Includes all internal user accounts in your organization.
Minimize the use of item-level permissions.
Similarly, you should prefer assigning permissions to higher-level containers like libraries or folders rather than to specific files or other items. Item-level permissions often result in broken inheritance and might be overlooked in permissions reviews, putting the security of SharePoint at risk. In addition, item-level permissions can slow down the search engine, impacting the user experience. Microsoft 365 features such as Information Rights Management (IRM) can reduce the need for item-level permissions.
Use separate site collections for external sharing.
A good way to keep users from inadvertently sharing sensitive content with external users is to isolate all sites that allow external sharing into one site collection. That way, you can more easily control what can and cannot be shared externally, and also track external sharing activity so you know exactly what has been shared and which external parties were given access.
Control anonymous sharing.
Disable anonymous sharing if possible.
It is also wise to disallow the sharing of content via anonymous links (also called Anyone links). These links enable anyone who has the link to view and even edit the content — with no authentication required.
If you allow anonymous sharing, reduce your risk.
If you decide you do not want to eliminate the use of anonymous links entirely, you can still reduce the risk that users will use them unintentionally by managing them carefully.
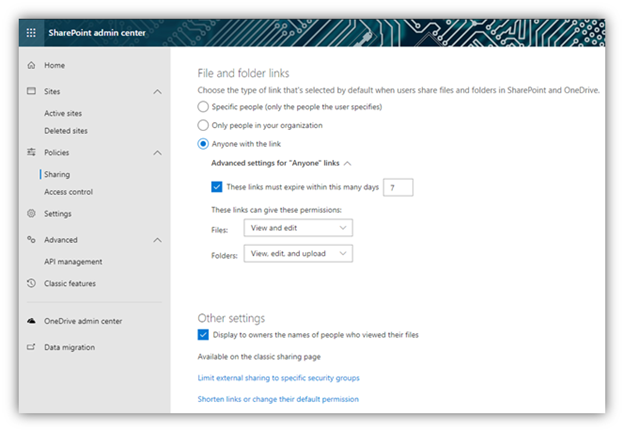
First, change the default link setting from Anyone to a link that works only for users inside your organization. That way, anyone who wants to share content with unauthenticated people will have to explicitly select the Anyone option.
In addition, you can apply settings that control type of access allowed via the link and specify an expiration date. To specify these settings, open the SharePoint Admin center and in the Policies section, click Sharing:
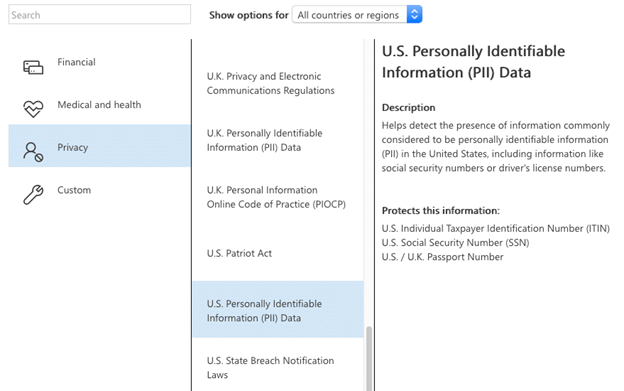
Most organizations understand the need to classify their data so they can control the use of sensitive and confidential content in accordance with internal security policies and industry or government mandates. Data loss prevention (DLP) technology can identify sensitive data and then block or allow access to it according to your policies. DLP is integrated into all Microsoft 365 services; in particular, SharePoint enables you to inspect the content, metadata and location of data and then apply security policies you have created to protect it, as shown below. To identify and secure sensitive content in your on-premises SharePoint, you’ll need a third-party data classification solution.
SharePoint is a highly dynamic environment, so you can’t simply set it up and then forget about it. Instead, it’s critical to audit activity in SharePoint, including changes to services, server hardware, virtual hardware and security settings, so you can quickly spot issues that could lead to breaches and business disruption. To ensure the best threat detection, investigation and response, you should supplement the built-in features with a solid third-party SharePoint monitoring tool.
Regularly review access rights.
Another vital step in maintaining MS SharePoint security is to regularly review access rights to your content, especially rights granted to the large groups detailed earlier.
If you are using SharePoint Server, you can manually check the permissions level granted to a group, as shown below:
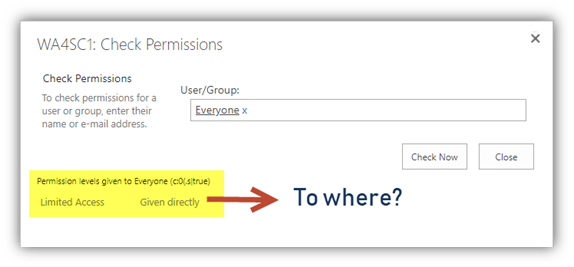
However, this will not tell you which IT resources the group has access to. To find out, you must check each library, list and file individually — a tedious process that that is extremely prone to human error and that busy IT teams rarely have time to perform.
To automate the process, you can use PowerShell scripts from sites like http://sharepointchips.com. For example, the script shown below will give a complete list of all the users and groups for a given site collection:
$sites = Get-SPWebApplication http://WebApplicationURL | Get-SPSite -limit all
"Site Collection`t Group`t User Name`t User Login" | out-file groupmembersreport.csv
foreach($site in $sites)
{
foreach($sitegroup in $site.RootWeb.SiteGroups)
{
foreach($user in $sitegroup.Users)
{
"$($site.url) `t $($sitegroup.Name) `t $($user.displayname) `t $($user) " | out-file groupmembersreport.csv -append
}
}
$site.Dispose()
}
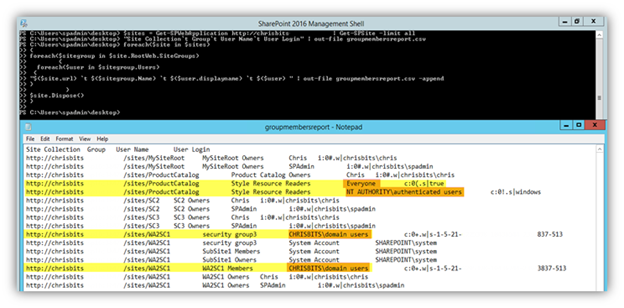
The output is exported to a CSV file in the directory that the command was run from. The sample report below highlights are some open access groups that you may discover have access to your site collection:
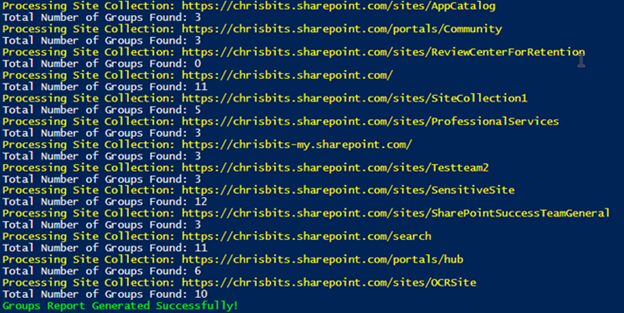
You can run PowerShell scripts for SharePoint Online as well, such as the script below from http://www.sharepointdiary.com:
#Admin Center & Site collection URL, replace admin-URL and path to a location where the CSV report can be written to.
$AdminCenterURL = "https://HOSTNAME-admin.sharepoint.com"
$CSVPath = "C:\Users\UserName\Documents\GroupReport.csv"
#Connect to SharePoint Online
Connect-SPOService -url $AdminCenterURL -Credential (Get-Credential)
$GroupsData = @()
#Get all Site collections
Get-SPOSite -Limit ALL | ForEach-Object {
Write-Host -f Yellow "Processing Site Collection:"$_.URL
#Get all Site Groups
$SiteGroups = Get-SPOSiteGroup -Site $_.URL
Write-host "Total Number of Groups Found:"$SiteGroups.Count
ForEach($Group in $SiteGroups)
{
$GroupsData += New-Object PSObject -Property @{
'Site URL' = $_.URL
'Group Name' = $Group.Title
'Permissions' = $Group.Roles -join ","
'Users' = $Group.Users -join ","
}
}
}
#Export the data to CSV
$GroupsData | Export-Csv $CSVPath -NoTypeInformation
Write-host -f Green "Groups Report Generated Successfully!"
How Netwrix Can Help
Netwrix StealthAUDIT for SharePoint delivers the robust SharePoint security features required to prevent data breaches, avoid business disruptions and satisfy modern compliance requirements. It delivers full visibility into SharePoint permissions at every level, in both on-premises SharePoint and SharePoint Online.


.png)