Amazon Web Services (AWS) is the world’s largest cloud provider, with well over a million active users. The popularity of AWS makes it one of the biggest targets for cybercriminals — and one of the leading contributors to breaches is incorrectly configured Amazon S3 buckets. For example, an insecure bucket led to the unauthorized access of 23 million documents and 6.5 TB of data belonging to Pegasus Airlines.
But what exactly are Amazon S3 buckets, and what can organizations that use them do in order to avoid being the next headline? This article answers those vital questions.
What are Amazon S3 buckets?
Amazon Simple Storage Service (Amazon S3) is an AWS cloud storage service that enables organizations of all sizes to store large amounts of data for a variety of use purposes, including websites, mobile applications, disaster recovery and big data analytics. Organizations are migrating their on-prem data to Amazon S3 to eliminate capitalization costs and achieve greater agility, scalability, availability and resiliency.
Buckets and Objects
Two core elements in Amazon S3 are objects and buckets. An object is a file and its metadata, and a bucket is a container for objects. Objects are uploaded to a bucket, and then they can be opened, downloaded or moved to another bucket. The screenshot below shows a bucket with two objects:
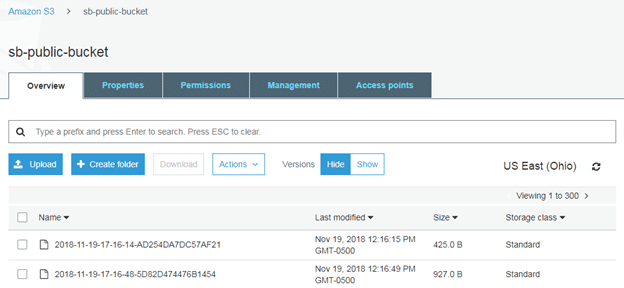
Figure 1: An Amazon S3 bucket with two objects
Access Management
Amazon S3 offers multiple features to control access to the data you store there:
- Access points are named network endpoints that are attached to buckets. Each access point has specific permissions and network controls that are applied to all requests made through it.
- Bucket policies provide granular controls to restrict object access to only those users that have the appropriate permissions.
- Access control lists (ACLs) can grant read and write permission for buckets and objects; however, Amazon recommends their use only in unusual situations in which you need to control access for each object individually.
- Identity and access management (IAM) controls help you manage permissions and access to your AWS resources. For example, Access Analyzer helps you establish and enforce a least-privilege model.
- Object Ownership is a bucket-level setting that you can use to control ownership of objects uploaded to a bucket. By default, when an object is uploaded to an S3 bucket, the account that uploaded the object owns the object, has access to it and can grant other users access to it using ACLs; you can change this default behavior using Object Ownership.
A Common Case of Breaches: Public Access
Most security breaches involving S3 buckets are due to the public access configurations assigned to buckets or objects. Public access means that that anyone who knows the name of an Amazon resource (ARN) can access it. The screenshot below shows a bucket for which public access is granted:
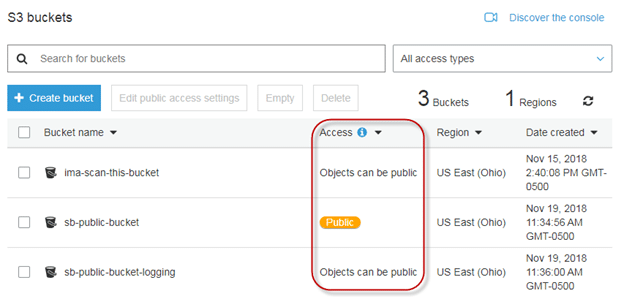
Figure 2: Public Access to an S3 Bucket
The primary methods for granting public access are:
- Bucket ACLs — You can use bucket ACLs to granularly assign access permissions, including READ, READ_ACP, WRITE, WRITE_ACP and FULL_PERMISSION. However, predefined ACLs provide an easy way to set up global permissions in one shot. One example is the Private ACL, which is applied by default to newly created buckets. Another example is the PUBLIC-READ ACL, which essentially makes a bucket public. Access permissions can be assigned to both users and groups, but it is a best practice to avoid granting permissions to default groups such as AuthenticatedUsers or AllUsers.
- Bucket policies — Bucket policies override bucket ACLs and are evaluated first. This means that a bucket policy allowing public access supersedes a bucket ACL set to PRIVATE.
- Object ACLs — Objects ACLs are used to grant different access levels to objects in the same bucket. Even if the bucket ACL is set to private, you can make specific objects in it public, though users would need to know the full path to those objects. If an object’s unique identifier is explicitly blocked in a higher policy, then the request is blocked. Otherwise, the object ACL is evaluated.
Again, it should be emphasized that Amazon recommends disabling ACLS except in specific rare circumstances. You can disable ACLs using Object Ownership.
How to Block Public Access to Your Amazon S3 Data
To block unauthorized users from accessing the data you store in Amazon S3, you can use the Block public access settings shown here:
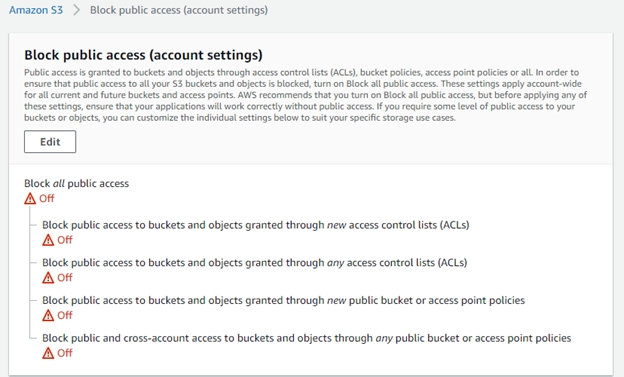
Figure 3: Block public access settings
There are four options available to limit public access:
- Block public access to buckets and objects granted through new access control lists (ACLs) — Prevents the creation of new ACLS that permit public access, without impacting existing buckets
- Block public access to buckets and objects granted through any access control lists (ACLs) — Prevents the creation of new ACLS that permit public access and overrides existing bucket ACLs that permit public access
- Block public access to buckets and objects granted through new public bucket or access point policies — Prevents the creation of future IAM policies that permit public access without impacting existing buckets
- Block public and cross-account access to buckets and objects through any publicbucket or access point policies — Prevents the creation of future IAM policies that permit public access and overrides existing policies that permit public access
While these settings can be applied for individual access points and buckets, the easiest way to prevent unwanted public access is to enable these configuration options at the account level. Of course, you should first ensure that your applications will work correctly without public access.
What if public access cannot be disabled at the account level?
While denying public access at the account level is highly recommended, it isn’t always possible, such as with the hosting of a static website. In these instances, consider using the following options to avoid unauthorized access to your S3 data:
- Instead of using a deny list strategy, take an allow list approach in which you to grant access to specific individuals.
- Apply write permissions sparingly. In particular, avoid using default groups such as Authenticated Users or All Users, which are too expansive.
- Use tools like Access Analyzer to monitor the effectiveness of your bucket access policies.
How Netwrix Can Help
Cloud storage platforms like Amazon S3 are great options for organizations that want to offload the burdens associated with on-premises data storage. However, the burden of securing your data storage repositories remains your responsibility. That’s why it pays to take a proactive approach when it comes to securing your most sensitive data. Netwrix StealthAUDIT reduces the risk to data stored in Amazon S3 through automated auditing and reporting of S3 permissions, file activity and data access. More broadly, it gives you a consolidated view of user access rights across your structured and unstructured data resources, both on premises and in the cloud.


.png)